Data breaches can have devastating consequences for either a user or website. Many platforms turned to magic link and OTP (besides using a password) to counter these events and protect users’ online accounts. At present, many companies are using two-factor authentication (2FA) to ensure no unauthorized party has access. For instance, recently, Google announced that they are planning to make two-factor authentication default for users; so many businesses are obligated to implement it.
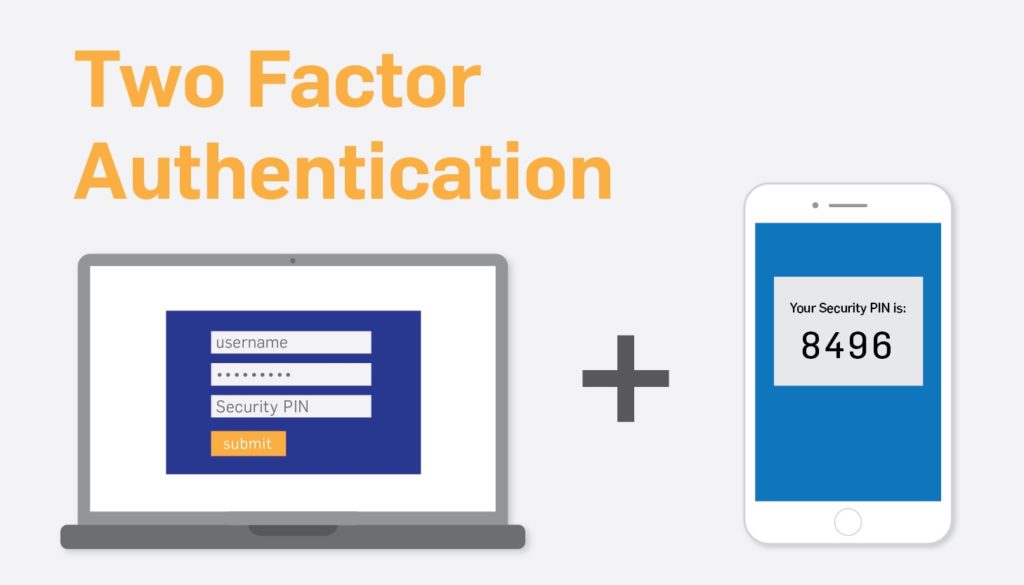
Two-factor authentication (2FA) verifies that the person trying to access a device and account is who they say they are. It is a security feature available on devices or applications and standalone app also known as authenticator. Two-factor authentication may also be called multi-factor authentication (MFA), two-step authentication and two-factor verification process. In short, the first factor is something you know, like username and password and the second factor is something you have, such as your smart-phone.
There are three types for evidence to confirm an identity and Two-factor authentication uses two of them. These identity-confirming types of evidence include:
How does 2FA work?
Two-factor verification works by using two elements to verify your identity before you can sign in for the application and device. This type of identity verification requires for the user to enter their name and password and then complete a second step to access an online account.
The second verification step usually consists of a randomized six-digit code and time-based one-time password (OTP). Some services also offer biometrics factors, like fingerprint.
In some cases, you sign in to your account for online with your username and password. After which, you receive a text message with a six-digit code. Once you enter the code into Google and Facebook, to proceed for your account.
Here are many common misconceptions about how secure is Two-factor authentication
The implementation of Two-factor authentication by many companies as the only security measure has been a source of concern. These experts claim that the concept of Two-factor authentication is misunderstood.
1. It isn’t susceptible to common cyber threats.
Two-factor authentication can be vulnerable for several attacks from hackers because the user can accidentally approve access to a request issued by a hacker without acknowledging it. This is because the user may not receive push notifications by the app notifying them of what is being approved. The codes are sent through unreliable third-party mediums. The safety of sending a code through an SMS message can depend on the mobile provider.
2. The implementation of 2FA can be considered for quick fix for the security breach.
A security breach can have lasting consequences on the reputation of a platform. This is because there are two negative outcomes. The first is one has to obtain a token and cryptic password sent through text message. The sudden requirement of Two-factor authentication may lead to the user being unable to log in. If it’s an optional logging method, most users will overlook how secure is Two-factor authentication and refrain from using it.
3. Almost every Two-factor authentication solution is similar, with minor differences.
There has been a vast difference in how secure is Two-factor authentication since the development of the concept. The authentication can take place by issuing an SMS, a verification link in one’s email account, and through other means. There are even cases where the 2FA process takes place automatically through keying information stored on the browser.
4. Most companies don’t care about how secure is Two-factor authentication but see it as a legal requirement.
Smaller companies mostly don’t spend for the significant amount of revenue on security. They create a makeshift security policy and loose usage of 2FA without understanding its security. Few companies view it as a hindrance to consumer experience since it requires for longer than usual login process.
Types of Two-factor authentication
There are manytypes of Two-factor authentication available, all of them relying on the different forms of factors including:
Lorem ipsum viverra feugiat. Pellen tesque libero ut justo, ultrices in ligula. Semper at. Lorem ipsum dolor sit amet elit. Non quae, fugiat nihil ad. Lorem ipsum dolor sit amet. Lorem ipsum init dolor sit, amet elit. Dolor ipsum non velit, culpa! elit ut et.
Lorem ipsum dolor sit amet elit. Velit beatae rem ullam dolore nisi esse quasi, sit amet. Lorem ipsum dolor sit amet elit.